Celo validator roundup, November 2020
Be aware of the slashing...
November has been the month of network upgrades for Celo. Successful rollout of core contracts upgrade delivered on the promise of iterative development and continuous improvements for the core protocol.
Overview
The trend has not changed and large amounts of CELO remains locked. Thus, overall expected APR from voter rewards continues to decrease.
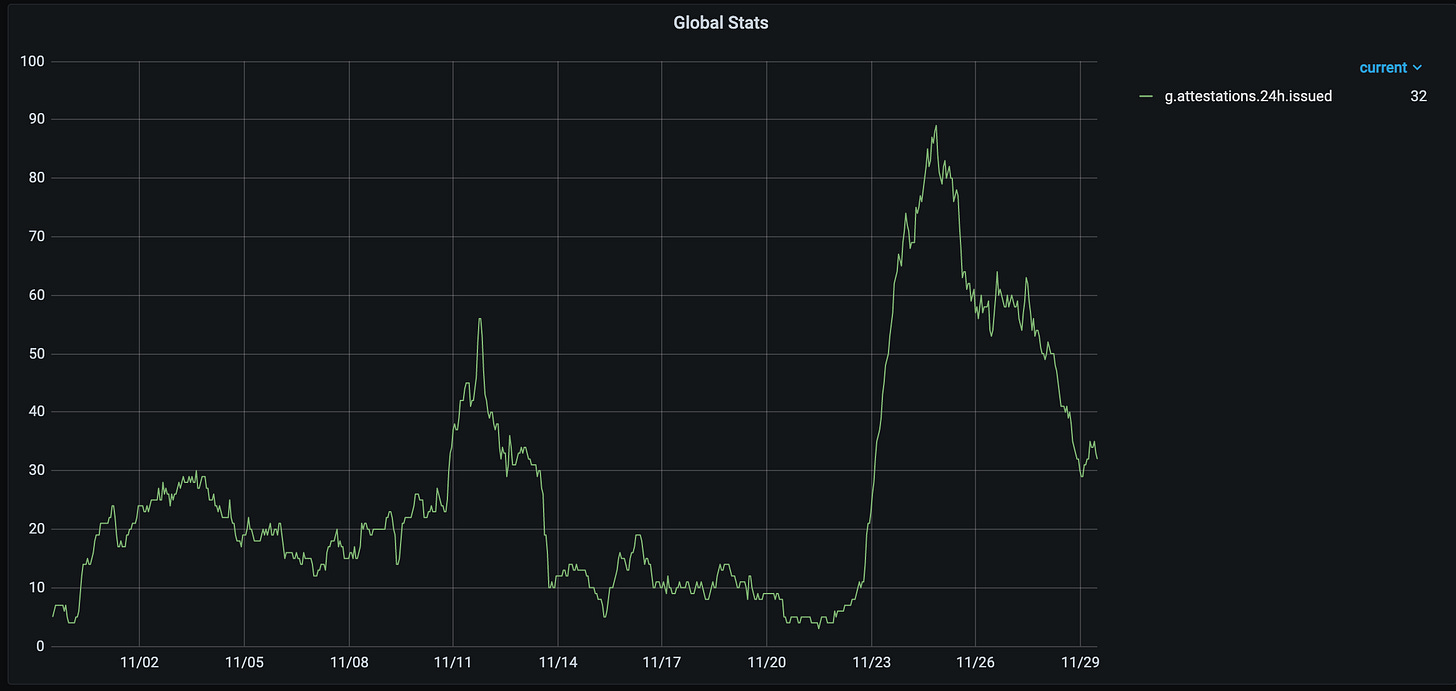
Registrations & Attestations
Overall growth of registered accounts and daily attestation requests remains roughly the same. There hasn’t been any large upticks or changes just yet.
cLabs team is now looking for ways to reward early users to help accelerate the growth and drive the engagement. Check out governance proposal for the discussion here: https://forum.celo.org/t/governance-proposal-to-reward-early-users/662
There seems to be small trend of improvement with attestation completions, however dataset is still way too small to be able to distinguish variance due to noise from real improvements. But this is still a positive sign overall:
Network Upgrades
Upgrades went much more smoothly this time around compared to previous attempts. Validators upgraded the blockchain client to 1.1.1, including various stability improvements and also a security fix for the GoLang standard library.
https://forum.celo.org/t/release-v1-1-0-of-celo-blockchain/616/3
https://forum.celo.org/t/golang-critical-security-update-for-validators-and-node-operators/679
Core contracts have also been upgrade to v1:
Core contracts upgrade sets the stage for all future improvements to the protocol. It has also fixed the long standing issue with the downtime slasher by replacing it with a new implementation.
Validator Performance
Network upgrades didn’t lead to any extensive downtime for most of the validator groups. But we still had three groups that crossed the slashing threshold:
Luckily for Bi23 and Sparkpool groups, the downtime slashing threshold has increased with the recent core contracts upgrade. Slashing threshold has increased from ~8 hours (5,760 blocks) of downtime to ~12 hours (8,640 blocks) instead.
Unfortunately for Alpha Virtual group, their downtime was larger than 12 hours and they were the first group to officially get slashed since the inception of the Celo network. As explained in the previous posts, slashing penalty provides quite a dramatic difference for the voter rewards APR. You can checkout the transaction that performed slashing in Celo Explorer: 0x05fa….0c5a.
This is probably an appropriate time to plug the Celovote service for regular users. If you don’t want to spend time manually monitoring the network and keeping track of the uptime for all your voted validators, you can just use Celovote instead and never have to worry about missing out on rewards due to validator downtime or their slashing penalties.
Next up…
Celo grants wave III should be distributed fairly soon. And Celo Community Fund is also close to becoming active, and hopefully will start distributing its own grants too in a month or two.
Looking forward to all the new projects and developments that get started due to these grants.